Why Should a Small/Mid-Sized Law Firm Worry So Much about Cybersecurity?
In a recent article, Managing Editor Zeljka Zorz of Help Net Security wrote:
“Businesses in the Professional Services industry (more specifically: law firms) have been heavily targeted by ransomware attackers.”
And you don’t have to look very hard to find evidence of that. In 2020, a banner year for ransomware, experts estimate that cybercriminals made off with $370 million in profits. The reality is (as the ever-growing list of victims of such attacks makes clear): Cybercriminals are actively targeting organizations of nearly all sizes. And law firms, with their access to highly sensitive data, are a prime target. But this blog post isn’t designed to be a scare tactic. Instead, we hope to help you better understand the steps you can take to mitigate your risk. Our goal is to do our small part in advancing broader cybersecurity awareness and education within the legal community, particularly given the exponentially escalating nature of these cyber-threats.
A Layered Approach to Security
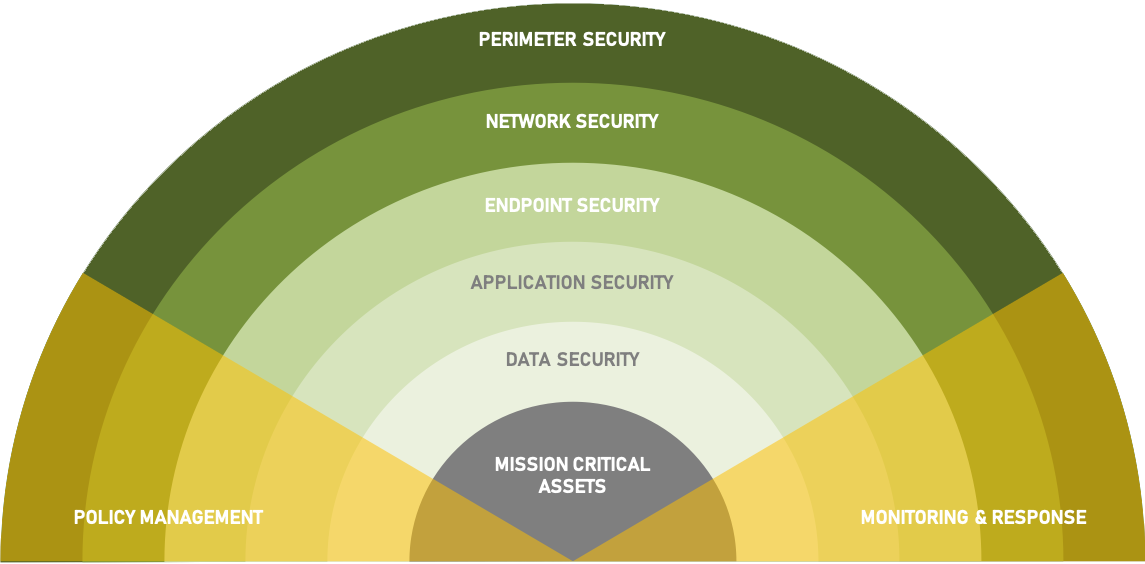
Over the next couple of months, you’ll be seeing a series of blog posts – from high-level security strategy highlights to security tools that law firms can use right now – that we hope will shine a light on different areas of security and provide law firms with key considerations and best practices to keep in mind. We’ll structure the discussion using a layered security model we have adopted for our own security roadmap. This includes:
- Perimeter Security
- Network Security
- Endpoint Security
- Application Security
- Data Security
- Policy Management & Enforcement
- Monitoring & Response
Within each security layer, we’ll explain that layer’s purpose, and highlight:
- Common security mistakes organizations can make
- Minimum security measures every organizations should take
- Best practices around security that organizations should consider
Some of our recommendations will be familiar – who hasn’t heard of multi-factor authentication? – but will be no less important for being familiar. (According to at least one survey, 78% of Microsoft 365 administrators do not have multi-factor authentication activated.) We’ll also talk about security philosophies and mindsets – least-privilege and zero-trust for example – and the steps you can take to help improve security in your organization – regardless who manages your IT infrastructure.
Shared Responsibility for Security
For too long, managed service providers and technology partners (including us) have taken the stance of shielding our clients from the headaches, intricacies, and complications that a strong security stance involves. While it’s true that we can significantly reduce the burden of security on our clients and their teams, the responsibility is still shared. We owe it to our clients to ensure they not only understand the steps we’re taking as their IT partner, but also the measures that require their active participation and consent. We hope this series of blog posts will help form the basis for those conversations, and we’re looking forward to more discussions to come.